Over the years there have been dozens of different jailbreaking methods and various hacks for Kindles, and every time Amazon closes one loophole someone discovers a new way to hack a Kindle’s software.
A good example of this recently came to light with something called KindleDrip.
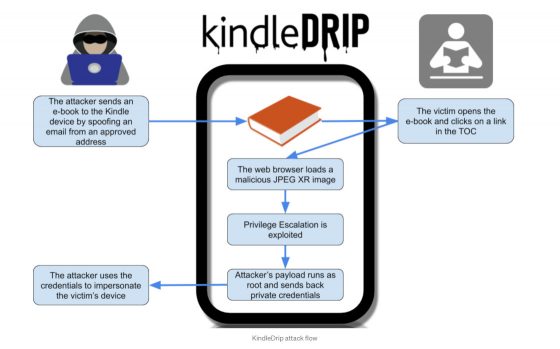
A researcher discovered three vulnerabilities in Kindle software that together can allow hackers to make purchases using your credit card, and they could also sell ebooks on the Kindle store and transfer money to their account.
All a hacker would need to figure out is your Kindle’s email address, which apparently isn’t that difficult to ascertain since it’s based on the regular email address you use for your Amazon account. Then they could send an ebook with links that open the web browser to a page that contains a malicious image that allow hackers access to private credentials from the device.
Amazon reportedly fixed the problem in the last 5.13.4 software update that was released in December, so if your Kindle is still running older software you might want to update it.
As noted in the conclusion of the KindleDrip article, this could also have been used to jailbreak the newest Kindle devices. Some people get frustrated by how closed down Kindle software is but reasons like this are why Amazon doesn’t want to keep any loopholes open and why they make hacking Kindles so difficult.
There haven’t been any reports of hackers using this method to get access to anyone’s accounts, but the video below shows what’s possible with the older firmware. The researcher reported the exploit to Amazon back in October and was awarded $18k in bounties.

Plugging security leaks and having a locked down device are two different issues imho even if the kindle was more free with the usage allowed they would still need to address security problems.
Also your article didn’t show any causal relation between this attack and jailbroken kindles.
From the conclusion of the linked article: “This could have allowed an attacker to access device credentials and make purchases on the Kindle store. This could also have been used to jailbreak the newest Kindle devices.”
How can Amazon allow Kindle software to be openly modified without opening up potential security risks?
I’m not for or against people modifying their Kindles; I’m just pointing out the obvious.
Yes since they chose to “secure” that a compromise in security will possibly allow you to change that.
However aren’t those risks present and managed on every other platform we use to make purchases on or payments with, which are all more open ?
There is an extra layer of protection in that you have to have the person’s email in your approved list of emails. There is a possibility if you use a general address that allows anyone to email you the book by just adding the domain address to your list, such as your workplace, which allows anyone to send you a book. I figure this would also be an issue if you side load a book. I was wondering how well does Amazon monitor the books they sell on their site since they have to handle so many books. Would it be possible to get a questionable book from Amazon?
Thank you, Nathan.
I appreciate your keeping me up to date on possible security issues.
I will update my Kindle now. 😊
You don’t mention the verification email – how does the hacker circumvent that? And why does Amazon even deliver the file to a kindle? They should just put it in your account and let you decides what device if any you want it delivered to, no?
When you use a Kindle’s specific email address the file goes to that Kindle.